Today we are going to discuss the excellent IPfire Linux router/firewall and how to run it incredibly cheaply and effectively on a Raspberry Pi B series device.
I have had my Pi B model for awhile now and it has been a neat experiment that I have done a few things with, but it hasn't really found a workload that I feel it is suited to at my house yet. XBMC was possible, but a let down and I am not a coder nor do I want to learn to code on my Pi. I wanted it to do work for me in a way I hadn't found yet.
Enter IPFire. They released an Arm port that runs on Pi and I knew I needed to try it out, as I have been running IPfire for years on typical x86 computers. It is excellent, feature filled, and stable.
Below is my completed Pi/IPfire setup. Yes it is a cabling mess.
See more info about what I do with my wall mounted setup here:
http://chuckscoolreviews.blogspot.com/2014/03/affordable-wall-mount-esx-5.html
To run IPfire on your Raspberry Pi, you will need:
-IPFire distro for Arm Processors: (free)
http://downloads.ipfire.org/latest (Choose Arm without serial console)
-A Raspberry Pi B or B+
-8 or more gigs SD card. I used 16 gig for mine. Get something as fast as you can afford. Sacrifice space for speed. Also consider whether you will be caching update files via Update Accelerator. This will take some space. Mine is eating 11 gigs now after some months in use.
-SD card reader for deploying the ipfire image
-IPfire supported USB Network interface card. See supported USB Nics here:
http://wiki.ipfire.org/en/hardware/networking
You might be asking yourself, self- why would I ever run a USB Nic? They are slow and I like fast. You might also be asking if the Pi is powerful enough to run your internet connection with as much speed as you think you need.
Let's discuss.
Yes USB Nics suck for LAN connections, but we are going to use it for your incoming WAN connection from your router. It just needs to be fast enough to manage your incoming internet speed. For most, this is 50 down/10 up megabits or less. USB2 will do 480 megabits of theoretical bandwidth, so it will not typically be your bottleneck. Now added to the fun is that the Pi saves money by running everything off of the USB bus. So the other built in Nic runs off of the same 480 megabits as your USB Nic. So let's say that halves your speeds, so each Nic gets 240 megabits from the Pi's USB bus. This is still faster than your provided internet, so your Network Interfaces will not be your bottleneck.
So now after the talk of theory, lets discuss how it handles in the real world with this config. Short answer: With a Raspberry Pi b+ providing my routing on a 50 megabit connection, the max download throughput I have seen is 25 megabits per second.
It IS the bottleneck. I find this to be acceptable mostly because I am invested into this solution and I like it. I don't really have need to go any faster than 25 megabits. The fact of the matter is that Cox has no speed offering that is right for me. It is either 5 megabits per second down or 50 megabits per second down. If they had something in between, this is where I would like to be. As it is, I have run the 5 megabits down and been satisfied with it.
Now you might be asking yourself, why go through all of the trouble of running your router on a Pi when your existing router is getting the job done?
Well, there are tons of interesting features that IPfire offers above and beyond what you can do on a typical router device, even one with Tomato or DDWRT firmware.
Take a look at the details page for IPfire and the addons to see them all, but my personal favorites are built in:
Transparent proxy with caching
URL Filter that works with whatever blacklist you want
Update Accelerator for caching updates for Windows, Linux, Antivirus Updates, and many other apps locally on the IPfire device saving you time and bandwidth. (also customizable to cache any type of file you want in addition to the defaults)
Nice web interface and good bandwidth usage stats so that you know if you are going over your monthly data cap limit due to Netflix binge watching and the like.
Ok so I have you talked into looking into this further and you have the parts needed.
Download the IPFire and copy get it onto your SD card.
These are the instructions I used:
http://xathrya.web.id/blog/2013/05/14/installing-ipfire-on-raspberry-pi/
Attach USB Nic to your Pi and Pi to an HDMI device. (To not disrupt my computer stuff, I hooked mine up temporarily to my TV.)
Boot and configure the IPfire from the interface provided via keyboard. No mouse needed. I set red network to USB Nic and Green network to built in NIC.
Boom, done with initial configuration. Now you need to hook the Pi to your network and see it go. No need for HDMI any more, you should be able to pull up the web interface once it boots. (Give it a couple of minutes to boot.)
Find it at:
https://green-ip-you-set:444/
Configuration of your IPfire and considerations for Pi:
Please note that I am going to cover items that I have enabled and changed as a result of running IPfire on a Pi device, but you can see full explanations of every setting on this IPfire wiki if you aren't sure or want more information about a setting or what does what.
http://wiki.ipfire.org/en/configuration/start
I like to go to pakfire section and install nano and htop. Nano is an easier way to edit txt files on the IPfire. (You should never have to do this though, but if you do this is easier than vi.) and htop is a much more informative process, cpu and ram monitor than the standard top application. There are tons of other items you can choose, most of which you probably shouldn't be running on your firewall/router, but nice that you CAN if you want to.
You will see that most spots for logging are already turned off. This is to save your SD card. SD cards are not as robust as hard drives, so limiting reads and writes where not necessary for troubleshooting is desired.
I also set mine to send syslog data to a VM I have running Linux and Splunk. Splunk is free for home use and for up to 500 megs of log files to process per day. I don't generate any where near 500 megs of log files across all of my devices that send logs to it. Splunk is an amazing log searching and archiving application that you need.
I enable Webproxy and set if for transparent on green. You can note port and other stuff, but since it is working transparently, there is no need configure your workstations for proxy.
Leave filter process set to default of 10 and note check boxes for URL Filter and Update Accelerator. The +17 for URL Filter and other value here can be ignored. They are suggestions for additional processes when enabling these features. These will bring your Pi to its knees if you add these additional processes above the 10 I recommend for the Pi.
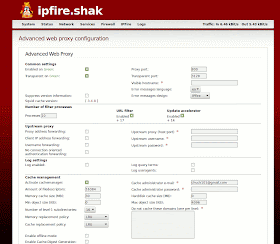
Now under Cache Management, you will see it is not enabled. You should enable this and make some selections here. Again, we want the best performance and least wear and tear on our SD card. SSHing into your IPfire and running htop right now tells us that your IPfire is using about 50 megs of the 512 megs installed RAM at this point in its operation, so you have RAM to donate to the cause.
I set mine to:
Enable Cache Management
Leave Default descriptors
Memory Cache: 30 megs =Fastest Option
Hard Disk Cache: 0 megs =Save that SD card from reads and writes!
Everything else in this section set to defaults include min object size 0 and max object size 4096.
See my config image below:
*When you make any changes on this page, choose save and restart button.
Be patient with the Pi. You won't be in here making tons of changes once you have yours configured, but when you do, they will take a few moments to apply. This is ok. As long as it is routing and firewalling effectively, who cares if the web interface that you should rarely use is a little slow. There has to be some Pi tradeoffs.....
The next item to configure is the URL filter.
This section is VERY important to not get nuttso on and enable all kinds of blacklists and stuff. This section is the spot that will murder your Pi !!!!1!
You can block based on URL categories and have a party in here blocking shadiness on the web.
I recommend checking out this blog page where I discuss nothing but this section and blacklists. Again, these are very important to understand and configure smartly.
http://chuckscoolreviews.blogspot.com/2015/01/clear-blacklist-in-ipfire-firewall.html
Next we need to configure Update Accelerator:
I like to set the following here:
Lower CPU Priority for downloads
Enable Automatic Source Check up Weekly
Replace Outdated Files during check up.
Also one checkbox worth mentioning:
Do not Check - Enable passive mode unless you want your Update Accelerator to pause functioning. That is what this box means. It stops caching and serving data if you check this box.
Now that you have all three items configured, go back to Webproxy and check the boxes to enable URLfilter and Update Accelerator. Choose save and restart. If you have enabled a bunch of blacklist stuff, expect that this will take a while to start. Be very cautious about enabling big blacklists! If you gotta have them all enabled, use something other than a Raspberry Pi for your router. (I am just blocking ads and virus infected categories at the moment on mine.) Porn and other shadiness, I block with a free OpenDNS.com account configured as such.)
Another item I like to enable and configure on my IPFire devices is weekly reboots. I also do this on any hardware routers where I have Tomato installed. I just think that this is a bit of preventive maintenance. Linux is stable and excellent, but usually the hardware that router devices and IPfire are running on are questionable. Rebooting them is not a bad idea.....
The spot for this isn't exactly clear on the IPfire. To make this change, go to:
Network | Connection Scheduler
In here, create a new task for rebooting at some time when no one at your house will be awake. Choose task: Reboot.
You are done. Enjoy your router!


This is great but I had some questions. I anted to know what is the major factor that is slowing down the throughput on this, is it the processor or the ram?
ReplyDeleteI think the issues are the CPU and the USB bus that is shared between the onboard NIC and USB NIC. See my guide for installing IPFire onto a Banana Pi if you really want to use IPFire on a Pi like board. It runs very fast and smooth on the banana pi with no issues whatsoever. Installation isn't as easy, but possible and the result is a night and day difference between the two devices.
DeleteHere is the link to that BPi guide.
Deletehttp://chuckscoolreviews.blogspot.com/2015/03/ipfire-on-banana-pi.html
Chuck'S Cool Reviews And Info: Ipfire Feature Filled Linux Firewall Router On Raspberry Pi B Or B+ Install And Config Guide >>>>> Download Now
Delete>>>>> Download Full
Chuck'S Cool Reviews And Info: Ipfire Feature Filled Linux Firewall Router On Raspberry Pi B Or B+ Install And Config Guide >>>>> Download LINK
>>>>> Download Now
Chuck'S Cool Reviews And Info: Ipfire Feature Filled Linux Firewall Router On Raspberry Pi B Or B+ Install And Config Guide >>>>> Download Full
>>>>> Download LINK 8z
Hello
ReplyDeleteHow did you manage to configure ipfire with splunk ?
I can't install Splunk Universal forwarder on ipfire ..
Thank for your help
I am not sure the Universal Forwarder runs on the IPFire. I set the Splunk IP address into the log server spot on the IPFire so that Splunk gets these logs. It is not as flexible as the Universal Forwarder, but it is better than nothing.
DeleteHi .. thanks
DeleteCould you tell me which file to modify in IPFire ?
Or did you change something in ipfire gui ?
Thanks for your help
Set this from the web interface. See link provided below to the IPFire Wiki page explaining this.
DeleteEnable syslog and enter the IP or hostname of your Splunk server. (Also make sure you have the syslog port enabled on the Splunk server. This is UDP 514.)
http://wiki.ipfire.org/en/configuration/logs/logsettings
Hi
DeleteYou're right ... I totally forgot how to do this
Thank again :)
It's working fine
On Pi 3 (newest Pi) it doesn't seem to support. Is this correct? Can someone confirm?
ReplyDeleteChuck'S Cool Reviews And Info: Ipfire Feature Filled Linux Firewall Router On Raspberry Pi B Or B+ Install And Config Guide >>>>> Download Now
ReplyDelete>>>>> Download Full
Chuck'S Cool Reviews And Info: Ipfire Feature Filled Linux Firewall Router On Raspberry Pi B Or B+ Install And Config Guide >>>>> Download LINK
>>>>> Download Now
Chuck'S Cool Reviews And Info: Ipfire Feature Filled Linux Firewall Router On Raspberry Pi B Or B+ Install And Config Guide >>>>> Download Full
>>>>> Download LINK